Residual risk is an important but often misunderstood concept in third-party risk management. It refers to the level of risk that remains after your organization has implemented controls, safeguards, and policies to reduce exposure. In other words, it’s what’s left behind when you’ve done everything you can—yet vulnerabilities still exist.
Recognizing and addressing these lingering exposures is essential to protect your organization from vendor-related breaches, compliance failures, and operational disruptions.
What Is Residual Risk?
This refers to the level of exposure that remains after all known security measures and mitigation strategies have been applied. While controls such as encryption, firewalls, employee training, or vendor assessments reduce risk, they can’t eliminate it completely. This type of risk acknowledges that even well-defended environments still carry some level of exposure. This is not a sign of failure; residual risk is expected. The key is understanding what remains, monitoring it continuously, and deciding if the organization is willing to accept, transfer, or further reduce it.
Residual Risk Formula
A simple way to visualize this:
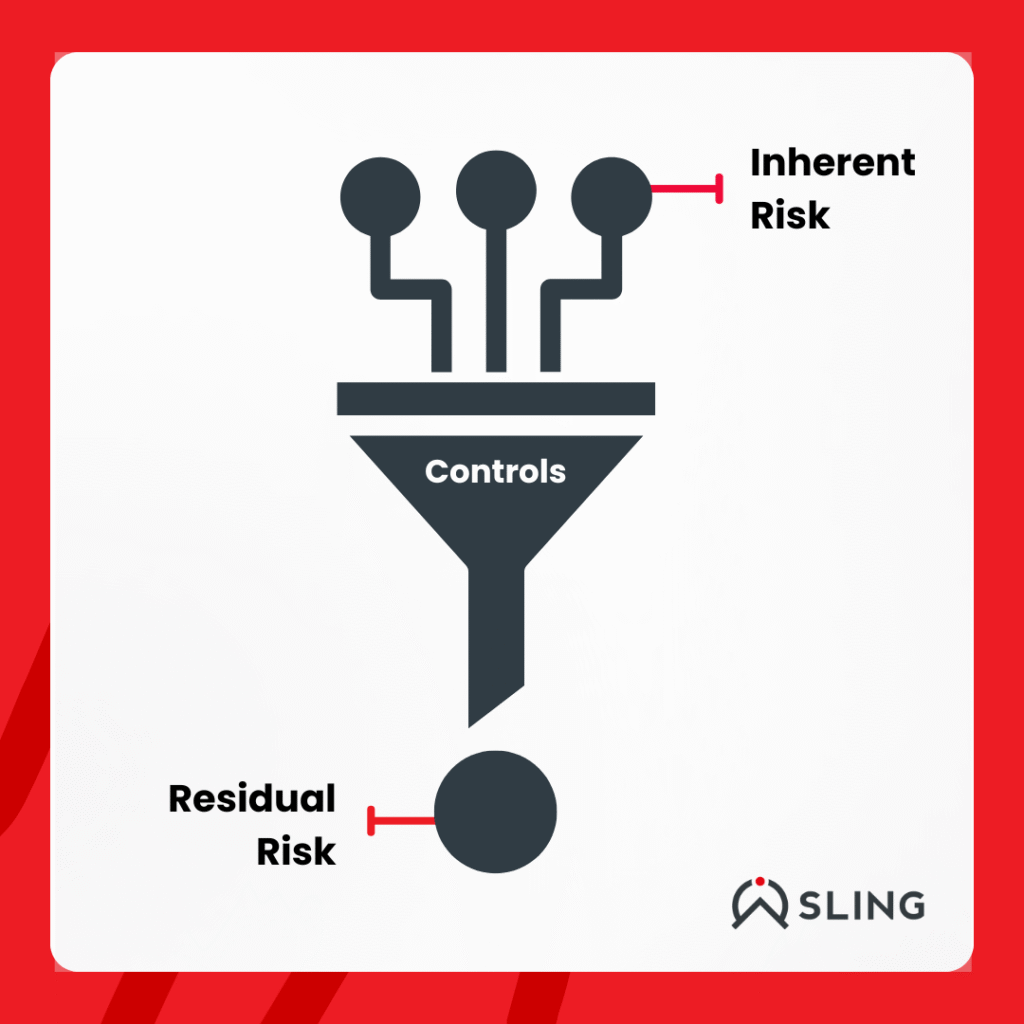
Residual Risk = Inherent Risk – Control Effectiveness
- Inherent Risk = the starting risk level without controls
- Control Effectiveness = the impact of safeguards put in place
Residual risk is never zero. The better your controls, the lower the it will be, but it always exists in some form.
Examples of Residual Risk
Residual risk shows up in many third-party scenarios, even when vendors seem secure on paper. Below are some practical examples of how it can persist despite control measures:
1. Misconfigured Systems
A cloud storage vendor uses encryption and access controls. However, a misconfigured bucket exposes sensitive files to the public. The inherent risk was reduced by controls, but residual risk persisted due to human error.
2. Expired Certificates
A trusted vendor’s SSL certificate expires, making its secure web portal vulnerable. The organization had controls in place, but residual risk remained because of a lapse in maintenance.
3. Unpatched Vulnerabilities
A third-party application has strong authentication in place. Houwever, an underlying framework remains unpatched, creating a potential initial access vector for attackers.
4. Vendor Expansion
Your vendor expands into new regions or adds new services. You’re unaware of the newly exposed assets. Even with controls, your visibility is outdated, and residual risk increases.
Key Takeaway
Residual risk often stems from what you don’t know; unseen exposures, outdated assumptions, or emerging threats.
Why Residual Risk is Critical to Third-Party Risk Management
Residual risk is more than a technical metric, it’s a business-critical signal. Understanding and tracking it helps organizations avoid costly blind spots and strengthens overall cyber resilience. Here’s why it matters:
1. Confirms Whether Controls Are Working
It highlights the effectiveness of your controls. A vendor might be compliant on paper, but real-world exposures, like unpatched servers or shadow subdomains, can still leave you vulnerable.
2. Supports Regulatory Compliance
Frameworks like NIST, DORA, and ISO 27001 emphasize ongoing risk evaluation. Regulators expect organizations to not only assess vendors before onboarding but also to monitor risk continuously.
3. Informs Risk Acceptance and Decision-Making
Helps executives decide:
- Is this risk within our tolerance?
- Can we transfer the risk (e.g., insurance)?
- Do we need to further mitigate it?
4. Enables Continuous Improvement
Residual risk isn’t static, it changes as vendors update infrastructure, attackers shift tactics, or new assets are added. Measuring it helps you adapt faster and maintain a proactive posture.
Residual vs. Inherent Risk: Know the Difference
To properly evaluate vendor exposure, it’s important to distinguish these two concepts:
Here’s how they differ:
| Attribute | Inherent Risk | Remaining Exposure (Residual) |
| When It’s Measured | Before any controls are applied | After controls are implemented |
| What It Reflects | Raw, natural exposure | Risk that remains after mitigation efforts |
| Purpose | Guides onboarding and risk tiering | Validates ongoing control effectiveness |
| Sling’s Role | Not assessed directly | Continuously monitored across company assets |
Sling helps you stay on top of residual risk by continuously monitoring your organization’s assets, identifying which vendors are associated with them, and flagging vulnerabilities or access points that may lead to compromise.
Measuring Residual Risk at Scale
As organizations work with dozens, or even hundreds of third-party vendors, manually assessing risk becomes impractical. Spreadsheets and static assessments only offer a snapshot in time. To truly manage risk, companies need scalable, real-time approaches.
Manual vs. Automated Residual Risk Assessment
| Method | Limitations | Benefits |
| Manual | Time-consuming, subjective, outdated | Low-cost, basic tracking |
| Automated | Real-time, objective, scalable | Continuous, context-aware data |
Manual assessments can help during onboarding, but often fail to reflect current exposure. Once a vendor is integrated, threats keep evolving.
How Sling Helps Measure Residual Risk
Sling automates risk measurement by:
- Discovering all external-facing assets and domains owned by your company
- Mapping each asset to third-party vendors with access or influence
- Identifying vulnerabilities, risks, and potential initial access points
- Issuing real-time alerts when new exposures are detected or risk levels shift
This approach gives teams a dynamic understanding of vendor-linked risks, so you’re not relying on static scores or outdated questionnaires.
Residual risk is the exposure that remains even after you’ve implemented controls and followed best practices. In the context of third-party relationships, it’s not just a technical metric, it’s the reality that even trusted, compliant vendors can still introduce vulnerabilities.
The challenge? These risks evolve constantly, often without notice. A vendor may deploy new services, change infrastructure, or introduce misconfigurations, without ever notifying you. That’s why relying on onboarding assessments or periodic reviews alone leaves your organization exposed.
Sling solves this by delivering continuous visibility into your true external risk. It automatically discovers all your company-owned assets and domains, identifies which vendors are connected to them, and highlights vulnerabilities or potential access points in real time. Instead of working with outdated snapshots, your team can monitor evolving third-party risks as they happen.
Risk will always exist, but with the right insight and tools, it becomes something you can measure, manage, and minimize with confidence.



